Key management
Proton Mail allows you to send and receive PGP encrypted emails without any technical knowledge or software installation. Encryption, decryption, and key management in Proton Mail are invisible to the user. However, Proton Mail gives advanced users the opportunity to import, export, backup, generate, and delete their own keys. This article explains how to manage your PGP keys in Proton Mail.
Your PGP keys
You can manage your private keys by signing in to your Proton Account at mail.proton.me(nouvelle fenêtre). Select Settings → All settings → Encryption and keys (in the left sidebar).

There are two categories of keys: email encryption keys and account keys. Each email address has its own set of keys, and there is one set of keys for account encryption. To see all the keys for a certain address or for your contacts, click on down arrow next to the dropdown menu at the top.

Proton Mail also allows you to import keys, generate keys, and export your public and private keys.
Key export (backup)
The Proton Mail web interface allows you to export your keys. You may want to do this in order to backup your keys in case you lose your password and lose access to your messages. In this case, you can import your exported keys and restore your ability to access your messages.
Your public keys are already displayed in the list. You can copy it to distribute this to your contacts. Your contacts can use it to send you PGP messages and to verify PGP messages that you are sending. Public keys cannot be used to decrypt your messages and thus cannot be used as a backup.
To export the private key of a certain address or contact, click on the down arrow under the Actions column and select Export private key. Because your private keys can be used to decrypt your emails, it is very important that your private keys are not leaked and that you do not import keys that somebody else has access to.
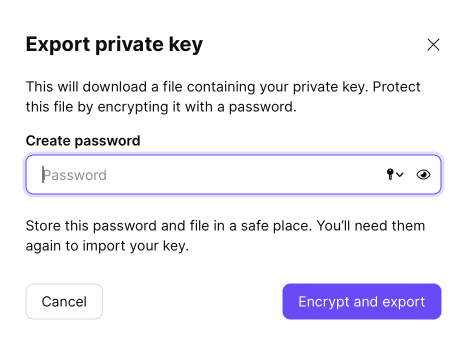
When you export your private key you will be asked for your current password, which will be used to decrypt your private key. Then, you will be asked for a new password to encrypt your exported key with. Make sure you keep this password safe, as you will need it to use this key!
Key import
Key import allows you to add existing PGP keys to one of your Proton Mail addresses. If you were using PGP on a migrated domain before you came to Proton Mail, you can import your old PGP key to seamlessly migrate your PGP setup to Proton Mail without having to redistribute your keys to your recipients. In the case of password loss, you can also import a backup key in order to restore access to that key and its associated mail. Key import is not supported for account keys.
There is a limit of 20 keys per address, so if you already have 20 keys you will need to delete one of the keys in your list in order to import another one.
To import a key for a certain address, click on the down arrow of the Generate key dropdown menu and select Import Key. Go through the dialog windows and select the key you want to import. If the key is encrypted you will be asked for the password.
If the key is a backup of an inactive key, the key will be activated. Otherwise, a new key will be added to your key set for that email address.
Note: Make sure that no one except you has access to the key you are trying to import. Never import a key generated by a third-party.
The new key is not used by default for encrypting new emails sent to you. To make the new key your default private key, you must set it as the primary key. We explain how to do this in the primary keys section below.
Key generation
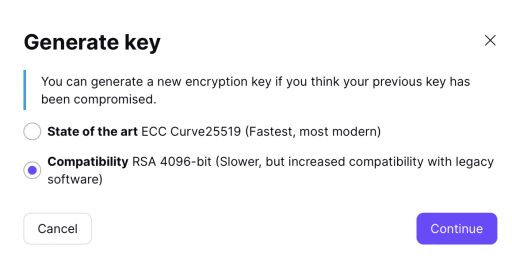
By default, Proton Mail will generate a set of keys when you create your account and anytime you create a new email address. When generating the key, you can choose between two different types of keys:
- ECC Curve25519 (Fastest, most modern)
- RSA-4096 (Suited for increased compatibility with legacy software)
The first type of key uses the elliptic curve cryptography (ECC)(nouvelle fenêtre) system known as X25519, which is fast, secure, and particularly resistant to timing attacks. Adding ECC keys(nouvelle fenêtre) is possible only after you have already created a Proton account.
The second type of keys will encrypt and sign your emails using RSA. RSA-4096 uses 4,096-bit keys, which provides an added security benefit but will cause decryption of your messages to be slower.
Generating additional keys after address creation is recommended if your existing keys have been leaked or have an undesirable key size.
Note that having multiple keys per address will slow down your login experience: each key has to be loaded and decrypted when you log in. There is a limit of 20 keys per address, so if you already have 20 keys, you will need to delete one of the keys in your list in order to generate more.
Key deletion
To reduce the number of keys in your account, you can also delete non-primary keys. This will speed up your loading times or free up space to be used for new keys.
You can delete a key by going into the key dropdown and clicking on DELETE. You will be asked if you want to export your key. We highly recommend you export your key, because once you delete this key you will not be able to access emails encrypted with this key. The only way to access these emails will be to import the exported key.
Key flags and settings
Primary keys
To request that your incoming emails are encrypted with your new key, you can make your new key the primary key. To do this, click the down arrow to the right of your new key and select Make primary. Making a key primary will also cause all your signed messages sent from this address to be signed with this key.
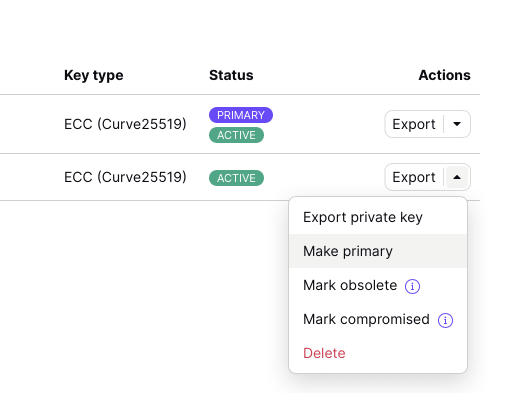
Obsolete keys
If your contact has trusted your keys, setting a different key as the primary key will not force your contacts to encrypt emails addressed to you with this new primary key. To force contacts to use the new primary key, you will have to mark the old trusted key as obsolete. This will block any Proton Mail user from sending with this key.
You can mark a key as obsolete by opening the key dropdown and clicking on Mark obselete. You can only mark a non-primary key as obsolete. You can mark an obsolete key as non-obsolete by opening the dropdown menu and selecting Mark not obsolete.
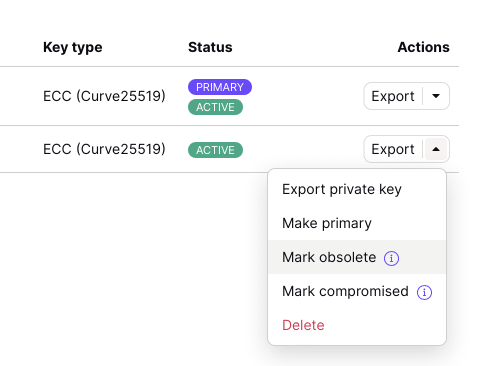
Compromised keys
It is also possible to flag your key as compromised. Not only will this block Proton Mail users from sending to you using this key, but this will additionally cause all internal Proton Mail messages signed with that key to fail signature verification. Note that signature verification is only enabled on your contacts’ side if they have key trusting enabled.
You can mark your key as compromised by going into the key dropdown and clicking on Mark compromised. You can only mark a non-primary key as compromised. A compromised key is always seen as obsolete. You can mark a compromised key as non-compromised by opening the key dropdown menu and selecting Mark not compromised.

